Cyber threats are increasing in scale, speed, and sophistication. In this environment, Managed Security Service Providers (MSSPs) are essential partners for organizations looking to protect their digital assets without building and maintaining full-scale security operations in-house.
But delivering effective cybersecurity services requires more than skilled analysts and advanced detection tools. It requires integration: connecting security platforms, ITSM systems, and customer environments so data flows automatically between them. Without that, MSSPs are stuck with manual handoffs, delayed incident responses, and siloed visibility.
This article covers what cybersecurity integration means for MSSPs, why it matters, how it improves operations, and how platforms like Exalate help MSSPs turn integration into a competitive advantage.
Key Takeaways
- MSSPs face a growing volume of complex cyber threats that demand faster, automated responses across multiple platforms and customer environments.
- Cybersecurity integration connects security tools, ITSM systems, and customer platforms to eliminate manual handoffs and information silos.
- Automated work item escalation between MSSP and customer systems reduces mean time to respond (MTTR) and improves SLA compliance.
- Integration acts as a competitive differentiator for MSSPs, allowing them to offer pre-built connectivity as part of their service packages.
- Security certifications, encrypted data transfer, and independent control for each party are non-negotiable features when choosing an integration solution for cybersecurity workflows.

The Current Cybersecurity Landscape for MSSPs
Cybersecurity has become a board-level priority for enterprises of all sizes and sectors. From ransomware attacks to supply chain compromises, cyber threats are growing in both frequency and complexity.
Modern IT environments, with their mix of cloud, on-premises, and hybrid infrastructure, create an expanded attack surface that internal security teams often struggle to cover on their own.
This is where Managed Security Service Providers (MSSPs) step in.
MSSPs deliver a broad range of security services, including threat detection, incident response, vulnerability management, and compliance assistance. They use technologies like AI-driven threat detection, machine learning models, and threat intelligence platforms to identify suspicious activities and potential breaches quickly. Most MSSPs offer 24/7 monitoring and expert guidance to help their clients meet compliance requirements like GDPR.
But the reality is that many MSSPs serve dozens or even hundreds of customers, each running different tools and platforms. A customer might use Jira for tracking security work items, while the MSSP runs ServiceNow internally.
Another customer might rely on Azure DevOps or Zendesk. Managing these diverse environments without integration means constant context-switching, manual data entry, and inevitable delays.
That is the exact problem cybersecurity integration solves.
What is Cybersecurity Integration?
Cybersecurity integration is the process of connecting various security tools, platforms, and practices into a unified workflow so that data, alerts, and responses move between systems automatically.
For MSSPs, this goes beyond simply having access to multiple tools. It means connecting those tools in a way that creates a seamless operational pipeline: from threat detection through incident response, all the way to resolution and reporting.
Here is what cybersecurity integration looks like in practice:
- Technology integration involves connecting your security stack, including firewalls, endpoint protection, intrusion detection systems (IDS), SIEM solutions, encryption tools, and IoT security layers, so they share data rather than operating in isolation. When a SIEM detects an anomaly, that alert should automatically create a work item in the appropriate system, assign it to the right team, and escalate based on severity. No manual steps involved.
- Threat intelligence integration means incorporating feeds from multiple threat intelligence sources into your operational workflow. Instead of analysts manually reviewing threat feeds, an integrated approach automatically correlates new threat indicators against existing customer environments. This allows MSSPs to identify risks proactively, before they escalate into active incidents.
- Compliance integration helps MSSPs ensure their clients meet regulatory requirements (GDPR and others) through automated reporting and continuous monitoring. Rather than compiling compliance reports manually at audit time, an integrated system continuously tracks compliance status and flags deviations in real time.
- Incident response integration connects the detection, assessment, and remediation phases of incident handling. When an incident is detected, the response process kicks off automatically: categorization, priority assignment, team notification, customer escalation, and status tracking all happen without someone copying data between systems.
- SOAR integration ties Security Orchestration, Automation, and Response platforms into the broader MSSP workflow. SOAR tools automate repetitive tasks like enriching alerts with context, isolating compromised endpoints, or updating firewall rules, then feed the results back into the MSSP’s ITSM system for tracking and customer visibility.
When these integration types work together, MSSPs operate with speed, accuracy, and consistency that manual processes simply cannot match.
Why Do MSSPs Need Integration?
Let us walk through a realistic scenario to see why integration matters so much.
An MSSP has its own incident management team that tracks all customer security incidents in ServiceNow. When a threat is detected, the team raises the incident with the customer’s IT or security team via email, a messenger app, or by manually creating a ticket in the customer’s system.
This works. But it is slow, error-prone, and does not scale.
Now consider the integrated alternative.
The MSSP detects a critical incident. That incident is automatically created as a work item in the customer’s Jira instance with a “Blocker” priority. The customer’s IT team starts working on it immediately.
Comments, attachments, status changes, and additional context flow back and forth between ServiceNow and Jira in real time. Neither team has to leave their own platform. The entire process runs end-to-end without manual intervention.
The same works in reverse. A customer raises an urgent security concern in their own system. The MSSP instantly receives the corresponding notification in their service desk, triggering an immediate response.
This level of automation is only possible with proper integration. And for MSSPs managing multiple customers across different platforms, such as Jira, ServiceNow, Azure DevOps, Zendesk, Freshservice, Freshdesk, Salesforce, or even custom proprietary systems, it is not a luxury. It is a requirement for delivering security services at scale.
The Importance of Integration in Cybersecurity Operations
When implemented correctly, cybersecurity integration does several concrete things for MSSPs:
- Eliminates information silos. Security data trapped in one tool is invisible to teams using another. Integration ensures everyone, on both the MSSP and customer side, works from the same information without duplicating effort.
- Reduces mean time to respond (MTTR). Automated escalation and real-time data exchange cut the delay between detection and response. For critical security incidents, even a few hours of delay can mean the difference between containment and a full-scale breach.
- Improves SLA compliance. Many MSSP contracts include strict SLAs around response and resolution times. Financial penalties for missed SLAs are common. Integration automates the tracking and escalation processes that keep MSSPs within their SLA commitments.
- Lowers operational costs. Automating routine but critical tasks (work item creation, status updates, notification routing, report generation) frees up security analysts to focus on higher-value activities like threat hunting and incident analysis.
- Strengthens compliance posture. Integrated workflows create consistent, traceable processes that simplify compliance. Automated data flows reduce the risk of human error in compliance-sensitive operations.
- Supports multi-tenant environments. MSSPs serve many customers simultaneously, each with unique tools and requirements. An integration solution that supports multi-tenant architectures allows MSSPs to manage all customer connections from their own environment while keeping each customer’s data and configuration isolated.
When evaluating how to improve cybersecurity operations, integration should be one of the first considerations, not an afterthought.
Exalate: a Secure Integration Solution for MSSPs
Exalate is a bidirectional integration platform designed for cross-company workflows, making it a strong fit for the MSSP use case.
It provides real-time, automatic synchronization between platforms like Jira, ServiceNow, Salesforce, Azure DevOps (Cloud and Server), Zendesk, GitHub, Freshservice, Freshdesk, Asana, and Jira Service Management.
For customers running proprietary or niche platforms, Exalate also supports custom connectors built via REST API, so the integration is not limited to pre-built options.
In addition, you can outsource your entire integration to Exalate’s managed services team, which handles the complexity of building, configuring, and monitoring integrations across multiple systems.
Exalate is ISO 27001:2022 certified, uses encrypted connections (TLS 1.2+), and supports role-based access controls and tokenized authentication. For a full view of Exalate’s security posture, certifications, and compliance documentation, visit the Trust Center.

How MSSPs Use Exalate as Their Competitive Advantage
Integration as a Service
MSSPs that include integration as part of their service package, rather than treating it as a separate project, build stronger customer relationships and reduce onboarding friction.
For example, if the MSSP uses ServiceNow and a customer uses JSM (Jira Service Management), a pre-built ServiceNow JSM integration becomes part of the service offering from day one. The customer does not have to source, build, or manage their own integration. They get seamless connectivity with the MSSP as part of the package.
This approach elevates customer trust, accelerates onboarding, and positions the MSSP as a full-service partner rather than just a monitoring vendor.
Independent Control for Each Party
Each side of an Exalate connection manages its own sync configuration independently. The MSSP defines what data it sends and how it processes incoming data. The customer does the same on their side. Neither party can override or access the other’s configuration.
This is important for cybersecurity integration specifically. In a cross-company setup, data privacy and access control are not optional. Each customer environment is isolated, meaning one customer’s data and integration logic is completely independent of another’s. There is no risk of cross-contamination between customer connections.
This setup also gives customers confidence that their internal data stays under their control. They decide what leaves their system and what comes in, without an external system having unrestricted access.
Scalability and Flexibility
MSSPs often start with a small number of customer integrations and need to scale as their client base grows. Exalate supports this through reusable integration templates that hold configurations for each customer separately.
Once an MSSP builds an integration template for a customer running, say, Jira, that template can be adapted and reused for other Jira customers without starting from scratch. The same applies when scaling to new platforms. Adding a Freshservice or Azure DevOps customer to an existing integration network does not require a fundamental redesign.
Exalate’s Groovy-based scripting engine lets MSSPs implement any integration scenario, from simple field mappings to complex conditional logic, multi-step escalation workflows, and dynamic routing.
For teams that want to move faster, Aida, Exalate’s AI-powered scripting and documentation assistant, generates sync configurations from natural language descriptions. This reduces the time needed to set up new customer integrations, especially for teams that are new to Exalate.
Think of it as a hub-and-spoke model: the MSSP system acts as the hub, and each customer system is a spoke. Adding new spokes is straightforward because the underlying architecture is built for it.
Reliability and Error Handling
Downtimes and system failures happen. In cybersecurity, even a few hours of missed synchronization can mean SLA breaches and unaddressed incidents.
Exalate addresses this with:
Automatic retry mechanisms that restore synchronization from the exact point of failure. If a connection drops, the system does not lose data. It picks up where it left off once the connection is restored.
Autonomous synchronization queues that preserve the order of operations. If multiple updates occur during an outage, they are processed in the correct sequence once sync resumes. This prevents data conflicts and ensures consistency.
Real-time synchronization capabilities that keep both sides of the connection current. For cybersecurity workflows where every minute counts, real-time data synchronization is essential.
How to Evaluate an Integration Solution for Cybersecurity Workflows
Choosing the right integration platform for cybersecurity operations requires more than checking a feature list. Here are the criteria MSSPs should prioritize:
- Bidirectional sync capability. One-way data pushes are not enough for cybersecurity workflows. Both the MSSP and the customer need to send and receive updates in real time.
- Broad platform support. Your customers use different tools. The integration platform needs to connect to the platforms you encounter most frequently (ServiceNow, Jira, Azure DevOps, Zendesk, Freshservice, Freshdesk, Salesforce, GitHub) and support custom connectors for everything else.
- Independent configuration for each party. In a cross-company integration, each side must control its own data flow without depending on or being restricted by the other side’s configuration.
- Security certifications and encrypted data transfer. At minimum, look for ISO 27001:2022, TLS 1.2+ encryption, role-based access controls, and tokenized authentication. The vendor should be transparent about their security posture, ideally through a public Trust Center or security documentation.
- Error handling and reliability. Integration in cybersecurity is not a “nice to have.” It is infrastructure. The platform must handle outages gracefully, with automatic retries and queue management that prevents data loss.
- Scalability across customers. Adding new customer connections should not require a full redesign. Look for template-based configuration, hub-and-spoke architecture, and the ability to manage multiple connections from a single environment.
- Flexible configuration options. Some integrations are simple, while others require complex conditional logic, data transformations, and multi-step workflows. Make sure the platform supports both without forcing you into a one-size-fits-all approach.
Use Cases for Cybersecurity Integration
Automating Work Item Escalation Between MSSP and Customer Systems
Case: An MSSP detects hundreds of security events daily across its customer base. Manually creating work items in each customer’s ITSM system is slow, error-prone, and does not scale.
Solution: The MSSP integrates its ServiceNow instance with each customer’s platform (Jira, Azure DevOps, Freshservice, Zendesk, or others) using Exalate. When a security event meets predefined criteria (severity level, event type, affected asset), a corresponding work item is automatically created in the customer’s system with the appropriate priority, category, and context.
Real-world application: Quorum Cyber, an MSSP, uses Exalate to automatically push security events (incidents, health monitoring alerts, vulnerabilities, and custom requests) to customers’ ITSM systems as part of their Managed Detection and Response service. Each customer’s integration is configured to their specific requirements, including customized data mappings and escalation rules.
Deep Work Item Integration as a Competitive Differentiator
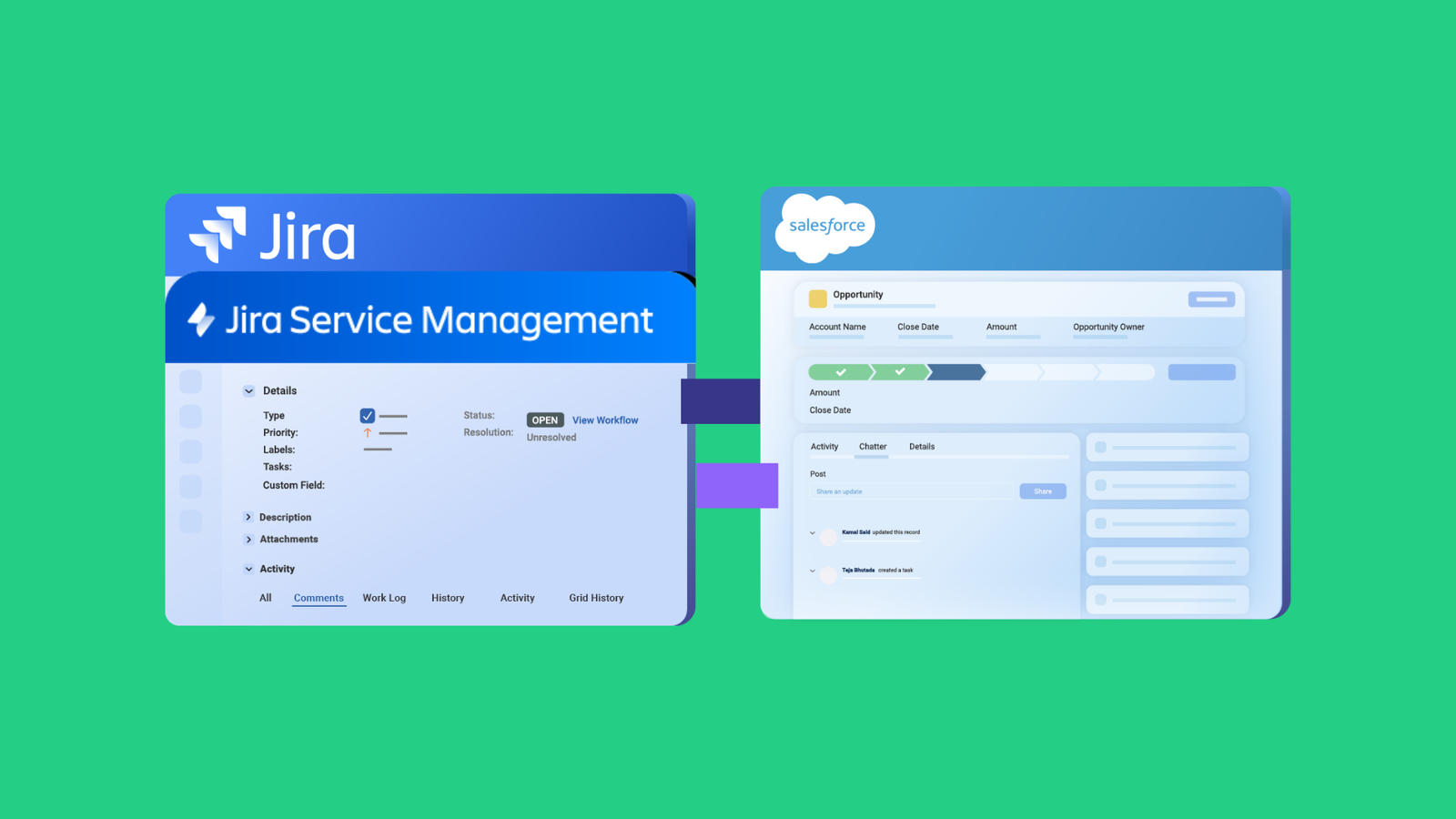
Case: A cybersecurity MSP needs to synchronize security incidents, vulnerabilities, and custom requests between its internal Jira and clients’ ServiceNow systems, with each client requiring different workflows and field mappings.
Solution: The MSP uses Exalate to create tailored Jira ServiceNow integrations for each client. Each connection has its own configuration, data mappings, and escalation logic, while the MSP manages all connections from its own environment.
Real-world application: NVISO, a prominent cybersecurity MSP, uses Exalate to bridge its Jira instance with clients’ ServiceNow environments. Customers receive security incident updates and manage their responses within their own familiar ITSM tools. NVISO’s integration setup supports regulatory compliance for sensitive client data in the EU, and new clients can join the integration network quickly because the platform is built for expansion.
SOC-to-Customer Escalation for Managed Detection and Response (MDR)
Case: An MDR provider’s SOC analysts identify threats across multiple customer environments but need a way to escalate critical findings to each customer’s incident management system instantly, without sharing credentials or requiring VPN access to customer systems.
Solution: The MDR provider connects its internal SIEM or service desk to each customer’s platform via Exalate. When a SOC analyst confirms a threat, a work item is automatically created in the customer’s system (Jira, ServiceNow, Azure DevOps, Freshservice, etc.) with full context: severity, affected assets, recommended actions, and attached evidence. The customer’s response updates flow back to the SOC in real time.
Real-world application: This pattern is common among MDR providers serving mid-market and enterprise customers. The public-private connectivity feature is especially valuable here, as most customer environments restrict inbound network access. The customer’s system pulls updates from the provider without opening inbound firewall ports.
Vulnerability Management and Remediation Tracking
Case: An MSSP performs regular vulnerability scans for its clients and needs to track remediation progress across multiple customer environments, each using a different platform.
Solution: Scan results from the MSSP’s vulnerability management platform are automatically synced to the appropriate customer system as work items with assigned priorities, affected systems, and remediation guidance. As the customer’s team addresses each vulnerability, status updates flow back to the MSSP for tracking and reporting.
Real-world application: An MSSP serving financial services clients uses this approach to sync vulnerability findings to customers’ Jira and ServiceNow instances. Remediation deadlines, priority changes, and resolution notes are tracked bidirectionally, giving both the MSSP and the customer a real-time view of the vulnerability management lifecycle without either party needing access to the other’s system.
The Role of AI in Cybersecurity Integration
AI is shaping both sides of the cybersecurity equation. On the threat side, adversaries use AI to develop more sophisticated attacks, automate reconnaissance, and generate convincing phishing campaigns at scale. On the defense side, AI powers threat detection, behavioral analytics, and automated response capabilities.
For integration specifically, AI is making it faster and easier to set up and maintain connections between platforms. AI-assisted configuration tools like Aida help MSSPs generate sync rules from plain language descriptions, reducing the time and expertise needed to onboard new customers. Instead of writing configuration scripts from scratch for every new client, an MSSP can describe the integration scenario and get a working configuration generated automatically.
That said, MSSPs should approach AI-driven outcomes with appropriate caution. AI-generated configurations should always be reviewed before deployment, and human oversight remains essential for security-critical workflows. The goal is to use AI to accelerate the operational work while keeping security decisions under human control.
Conclusion
As cyber threats grow in complexity and volume, the role of cybersecurity integration for MSSPs becomes more critical. The ability to automatically exchange security data between MSSP and customer environments, in real time, across different platforms, is what separates reactive security providers from proactive ones.
Solutions like Exalate give MSSPs the infrastructure to deliver that level of integration. Real-time bidirectional sync, broad platform support (including Jira, ServiceNow, Salesforce, Azure DevOps, Zendesk, Freshservice, Freshdesk, Asana, GitHub, and custom connectors), independent control for each party, and reliability features designed for mission-critical workflows.
With the right integration strategy, MSSPs can reduce response times, improve SLA compliance, scale their customer base efficiently, and turn integration itself into a service offering that differentiates them in the market.
To learn more about how Exalate can support your MSSP operations, get in touch with one of our integration experts.

Frequently Asked Questions
What is cybersecurity integration for MSSPs?
Cybersecurity integration for MSSPs is the process of connecting security tools, ITSM platforms, and customer environments so that security data, alerts, and incident updates flow between systems automatically. This eliminates manual handoffs, reduces response times, and gives both the MSSP and their customers visibility into the security workflow without leaving their own platforms.
How does Exalate help MSSPs with cybersecurity integration?
Exalate provides bidirectional, real-time synchronization between the MSSP’s platform (typically ServiceNow or Jira) and each customer’s system. Security events, work items, comments, attachments, and status changes sync automatically based on rules the MSSP configures. Each customer connection is independent, so adding or modifying one customer’s integration has no impact on others.
What platforms does Exalate support for MSSP integrations?
Exalate supports Jira Cloud, ServiceNow, Salesforce, Azure DevOps (Cloud and Server), Zendesk, GitHub, Freshservice, Freshdesk, Asana, and Jira Service Management. For platforms not covered by pre-built connectors, Exalate supports custom connectors built via REST API, so MSSPs can connect to virtually any system their customers use.
How does Exalate handle data security for MSSP integrations?
Exalate is ISO 27001:2022 certified, uses TLS 1.2+ encryption for all data in transit, and supports role-based access controls and tokenized authentication (JWT). Each side of a connection controls its own data flow independently, meaning no single point of failure exposes both systems. Full security documentation is available at the Trust Center.
What happens if a connection goes down during a cybersecurity incident?
Exalate includes automatic retry mechanisms and synchronization queues. If a connection drops, no data is lost. Updates are queued and processed in the correct order once the connection is restored. This ensures that even during outages, work item escalations and status updates are not missed.
Can MSSPs customize integrations for each customer?
Yes. Each customer connection has its own independent configuration. MSSPs can tailor field mappings, escalation rules, priority assignments, and data transformations to match each customer’s specific requirements. Exalate’s Groovy-based scripting engine supports any level of customization, and Aida (AI-assisted configuration) helps generate configurations from natural language descriptions.
How does integration improve SLA compliance for MSSPs?
By automating work item creation, escalation, and status tracking, integration removes the manual delays that cause SLA breaches. When a security incident is detected, the corresponding work item is created in the customer’s system instantly, with the correct priority and all relevant context. Response and resolution times are tracked automatically across both platforms.
Can Exalate support MSSP integrations with SOAR and SIEM platforms?
Exalate’s custom connector capabilities (via REST API) allow integration with SOAR and SIEM platforms that expose APIs. This means SOC teams can connect their detection and orchestration tools to the MSSP’s ITSM platform and, through that, to each customer’s system. The result is an end-to-end automated pipeline from threat detection through customer notification and resolution tracking.
How quickly can an MSSP deploy a new customer integration with Exalate?
Deployment time depends on complexity, but most standard customer integrations take hours rather than weeks. MSSPs that use reusable templates and AI-assisted configuration (Aida) can onboard new customers even faster, since much of the configuration groundwork has already been done for similar setups. Exalate’s managed integration services are also available for MSSPs that want to offload the setup entirely.
Recommended Reading:
- MSP Integration: Why It Matters for Your Business
- Jira ServiceNow Integration: How to Connect Jira and ServiceNow in 6 Steps
- ITSM Integration: Simplify Your IT Services Like Never Before
- Exploring the Working Principles of Service Desk Integration
- Integration as a Service (IaaS): Everything Explained
- Integration Security: Safeguarding Your Data in Connected Systems