In today’s interconnected world, integration has become the backbone of business operations. However, as data travels between platforms, safeguarding it becomes paramount.
In this blog post, we delve into the realm of Integration Security, exploring the vital measures and best practices to protect your data in the connected landscape.
So join us on this journey to ensure your data remains safe and secure throughout its integration adventure.
Understanding Integration Security
Integration is necessary to make your business teams and processes work together smoothly. It allows your systems and applications to talk to each other and ensure data exchange without any errors.
In the physical world, just like security guards protect your valuable assets and goods, in the virtual world, integration requires security measures to safeguard your valuable data.
Integration security refers to a set of measures and protocols implemented to ensure the secure transmission and processing of data between different platforms, companies, or teams. It makes the data exchanged between your interconnected systems safe and sound.
Securing your integration has a few main goals:
- Data Confidentiality. You need to ensure that sensitive business data like customer information, financial records, or intellectual property remains confidential and is accessible only to authorized parties in the integration process. This involves encrypting the data during storage and transit.
- Data Integrity. You need to ensure that the data remains unaltered and accurate during and after the integration is implemented. Integration security uses various techniques to check if your data remains unaltered during the exchange. It’s like giving your data a digital virtual fingerprint through hash functions and checksums to ensure it hasn’t been tampered with.
- Data Availability. Securing your integration will ensure your data is available when you need it. This involves data storage at multiple locations and regular backup mechanisms to avoid data loss or service interruptions due to hardware failures or cyber-attacks.
Having goals is a good starting point to secure integrations, but it also means you must be aware of how insecure integrations would impact your business.
How do Insecure Integrations Affect Businesses?
Insecure integrations can be a primary target for cybercriminals seeking to exploit vulnerabilities and gain unauthorized access to sensitive information. A successful data breach can lead to severe consequences, including financial losses, reputational damage, and legal implications for your business.
Lack of authentication and access control mechanisms can lead to users gaining access to critical systems. It can result in data manipulation, service disruptions, or even data theft.
Integrated data may get corrupted during transmission, leading to inaccurate information processing, in turn impacting business decisions and key insights.
Let’s look at an example of a popular retail corporation that faced a security breach and how it impacted its business.
Target Data Breach (2013)
In 2013, attackers gained access to Target’s networks through a third-party vendor’s credentials. The hackers exploited weak integration security between the vendor’s system and Target’s network to install malware on the point-of-sale (POS) systems. The breach compromised the credit and debit card information of over 40 million customers and the personal information of around 70 million individuals.
To minimize the business impact of insecure integrations, you must take into account a few challenges.
Common Integration Security Challenges
A few common integration security challenges that need attention are:
- Data mapping, transformation, and validation issues: Ensure the data you want to exchange is mapped accurately and is aligned between the systems under integration. Also, ensure it has been transformed correctly and adapted to the destination format and requirements. The exchanged data must be accurate and error-free.
- Complexities of integrating legacy systems with modern applications while maintaining security: Handling technology differences between legacy applications and modern ones requires thoughtful planning and implementation. Also, ensuring security measures are consistent across the entire integration ecosystem is paramount. You need a unified security approach to avoid weak links in the chain.
- Vulnerabilities and Patches: You must manage vulnerabilities and ensure the timely application of security patches across integrated systems.
- Identity Management: You need to ensure consistent identity management practices across all integrated systems.
- API Security: You need to ensure the Application Programming Interfaces (APIs) used for integration are protected against API-based attacks, like API injections or token-based vulnerabilities. You also need to be protected against brute-force attacks or denial-of-service (DoS and DDoS) attempts. These impact the performance and availability of the integrated systems.
Many of the above challenges we discussed exist for integrations across departments, teams, and applications within a single company.
But how do you handle security challenges posed in a Managed Service Provider or more importantly, in a Managed Security Service Provider setup?
Integration Security Challenges in an MSP or MSSP Setup
Intra-company integrations must be secure. There is no second-guessing here. But the security threats, challenges, and potential risks that exist when you connect with applications across company borders are exponential. This is because of the inherent nature of cross-company integrations, for instance, MSPs connecting with their customers and external systems.
We’ll see why this stands true by reflecting on some security challenges in an MSP environment:
- Filtering out internal and external information is essential. Before commencing the actual integration effort, it is essential to provide a detailed account of proper information classification and the methods to achieve it.
- Identifying messages containing private information and not pushing it across to the receiving system is important. This is especially true in an MSP setup where there are high chances of private information being sent over and misused.
- Assessing the security posture of third-party companies you want to integrate with is essential. This can also include certain compliance or regulatory requirements that the integration process with them must adhere to.
Note: You can explore how MSSPs like NVISO use secure integration solutions for deep ticket integration to gain a competitive advantage.
Addressing these challenges requires a comprehensive integration security strategy.
Best Practices for Secure Integration
You can enhance the security of integrations by following a few best practices:
Implement Authentication and Authorization
Employ Role-Based Access Control (RBAC) to ensure the right users have access to the integrated systems.
Use MFA (Multi-Factor Authentication) wherever possible for an added layer of security for user access.
Use Secure Communication Protocols
Employ secure protocols like HTTPS (TLS/ SSL) to ensure information is encrypted while in transit.
Use updated and strong encryption algorithms.
Secure APIs and Endpoints
Authenticate and authorize API calls so the right users can gain access to the APIs.
Use OAuth tokens, API keys, and JWT (or JSON Web tokens) for secure API access and authorization.
Monitor and Log Activity
Use robust monitoring mechanisms to record integration activities like API calls, user interactions, etc.
Enable log management to keep track of potentially suspicious activities and respond promptly to them.
Perform Regular Security Audits and Reviews
Conduct security audits/assessments and penetration testing on integrated systems to identify vulnerabilities.
Ensure timely security updates and patches.
You can think about developing a vulnerability management program in order to formalize your approach to auditing and monitoring integrated systems. It is easier to stay on top of security responsibilities if there is a clear framework in place for you to follow, and a determined set of tools and processes to implement.
Limit Data Exposure
Limit the data exposed through integrations to only what is necessary for the operation.
Apply data anonymity or pseudonymization techniques to protect sensitive data.
Establish Error Handling Mechanisms
Ensure proper error handling mechanisms are in place and no sensitive data is displayed in error messages.
Provide meaningful yet generic error messages.
Apply the Principle of Least Privilege
Grant the minimum required privileges to the user of the integrated system or service. This ensures users do not take advantage of their privilege and gain access to information not within their purview.
Secure the Data
The general approaches you can take for securing the data are:
- Use tokens to protect sensitive information. These are random data strings with no decipherable relationship to the original data. They are usually stored at an external data source.
- Mask data for unauthorized users. It means converting the data into a format that appears authentic but is useless to intruders. It includes shuffling, substituting, deleting, or scrambling the data.
- Encrypt the data during storage and transit. It includes converting plain text into ciphertext using secret encryption keys, ensuring secure transmission and decryption at the destination.
Train Employees and End Users
Conduct regular security awareness training to educate users, admins, and other stakeholders about integration security best practices.
Encourage them to report any suspicious activities or potential security threats.
Stay Updated With Security Best Practices
Stay informed about the latest security trends, industry standards, bugs, and vulnerabilities in the integrating systems.
It’s essential to ensure that security blends seamlessly with the integration process and the integrating systems become an innate aspect of the overall security.
While doing so, finding a secure integration solution is equally important.
Factors to Consider While Choosing a Secure Integration Solution
Here are some key factors to consider when selecting a secure integration solution:
- Standard security mechanisms: Tools that support the standard security mechanisms we discussed in the previous section:
- Authentication and Access control,
- Encryption,
- Vulnerability and Patch Management,
- ….
- Decentralized Integration: Integrations, like all aspects of technology, undergo continuous evolution. The challenge lies in managing evolving workflows that change only at one end of the integration. Decentralized integration offers a solution by granting you independent and granular control over your end of the integration. This allows you to maintain the confidentiality of shared information with external companies without having the burden of communicating every change to them. We’ll discuss this in detail later.
- Robustness: Tools that support robust integrations that withstand downtimes and system failures in a graceful manner are important. Having integrated retry mechanisms that start the integration from the point of failure will keep you secure against potential vulnerabilities and enhance data accuracy.
- Ease of integration and configuration: The tool must be easy to integrate with your existing systems and applications, minimizing the impact on your development and operational workflows.
- Scalability: Tools that can handle the required scale of your integration environment without compromising performance or introducing bottlenecks must be selected.
- Vendor Reputation and Support: Research the reputation of the tool’s vendor, read reviews, and ensure they offer customer support and regular updates to address emerging security concerns.
- Cost-effectiveness: Evaluate the total cost of ownership for the tool, including licensing fees, maintenance costs, and potential productivity gains or losses.
By carefully evaluating the integration solutions based on these factors, you can select the most suitable option to fortify your integration landscape.
One such solution we’ll discuss here is Exalate.
Exalate: A Third-party Tool Providing Secure Integrations in a Distinct Manner
Exalate is a fully customizable and secure integration solution that supports multiple popular platforms like Jira, Salesforce, Zendesk, Azure DevOps, GitHub, etc.
It implements all the standard security mechanisms like HTTPS, JWT-based tokens, role-based access control, etc.
But what makes it unique are some features we’ll discuss now.
Decentralized Integration
Exalate supports decentralized integration. With the help of specialized processors, it filters and transmits only the necessary information between applications. Thus, you can exclude sending or receiving unwanted data, as can your clients, ensuring both security and peace of mind at both ends.

In decentralized integration, both systems retain control over the information they share and handle incoming data selectively to prevent unauthorized access. The approach grants you full control over your sync without relying on the other side’s admin. It ensures a robust and resilient integration that can adapt locally without informing the other system. Such autonomy leads to fewer concerns about potential sync issues and system failure, making the integration more reliable and less susceptible to downtimes.
This is different from what most of the centralized solutions out there have to offer.
Distributed Architecture
Exalate maintains decentralized integration using a distributed architecture, where each integrating application has its own Exalate node that translates information exchanged between the systems.
In the following setup, there are two Exalate nodes, one for each tracker (e.g., Jira, Salesforce, ServiceNow).
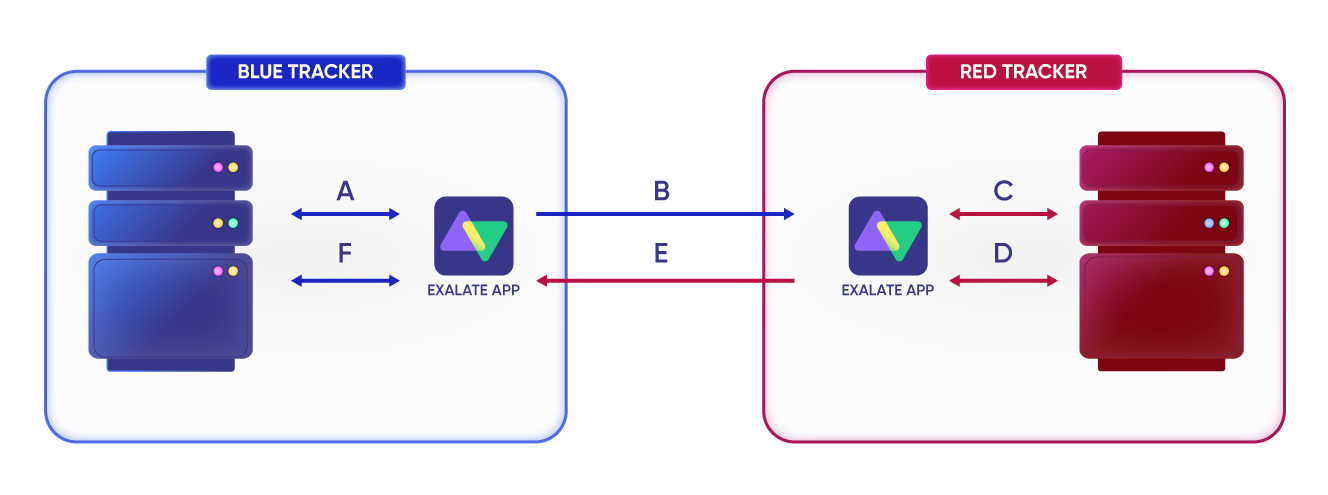
When synchronizing from the blue tracker to the red tracker, the information is securely sent to the blue tracker’s Exalate app, then transmitted to the red tracker’s Exalate app. After which, it is applied locally on the red tracker and then acknowledged back to the blue tracker.
Such a distributed approach ensures that both ends control access to their Exalate app and manage integration configurations independently.
For a detailed understanding of the Exalate architecture, refer to this security and architecture whitepaper.
Loosely Coupled Systems
Systems in a distributed environment are inherently loosely coupled. As integrations develop over time, having tightly coupled systems leads to unnecessary overheads and dependencies.
In a tightly coupled setup, the software components are dependent on each other, and the failure of a single component can lead to a cascading failure of the dependent ones. Loosely coupled systems can overcome such a single point of failure. They also enable us to modify a single component without affecting the other involved components. It makes the systems scalable, flexible, and easy to maintain, as you can add new integrations smoothly.
Single-Tenant Architecture
Most cloud deployments are implemented with a multi-tenant architecture, which uses shared infrastructure to fulfill necessary functions. Consequently, such an arrangement might run the risk of blending your data with that of your competitors, who might gain unauthorized access due to system bugs.
To mitigate this risk, the Exalate engineers made the decision to implement a single-tenant architecture.
Under this approach, each instance of the Exalate application and its corresponding environment supports only one application. Such an isolation ensures that every instance operates within its own distinct process space, file system, network, and database, entirely segregated from all other instances.
Secure by Design
Exalate integrates security vulnerability scanning at every step of its development, deployment, and operation. It proactively identifies security issues right from the moment a developer starts writing code, ensuring a robust and secure foundation for the entire system.
Sync Queues
Exalate uses sync queues on both integrating ends to enable an asynchronous sync process. Each sync event is processed through the sync queue and applied in the same order as its initiation at the other end. Such an approach guarantees that all modifications are implemented correctly, even during periods of system downtime or failure.

Additionally, Exalate incorporates a built-in retry mechanism, which facilitates recovery from any failures and allows the synchronization to continue seamlessly from the point of interruption.
Other Security Policies and Processes
Any customer data in the Exalate cloud is encrypted in transit and at rest. Offline backups are encrypted for each tenant.
In Exalate we choose to delegate the authentication and authorization to the underlying platform as this allows consistency (in access management).
You can report any vulnerability, concern, or incident either on the support portal or via an email to security@exalate.com.
Note: You can refer to our security questionnaire in case of any doubts.
Now we’ll explore the upcoming trends in integration security.
Future Trends in Integration Security
Technology has advanced, and businesses are becoming increasingly reliant on interconnected systems. So integration security is evolving to meet the growing challenges of safeguarding data and ensuring seamless transactions.
AI-Powered Insights in Threat Intelligence
Artificial Intelligence (AI) is revolutionizing the landscape of cybersecurity, and its potential impact on integration security is immense. AI-powered threat detection systems can continuously monitor data flows, patterns, and anomalies in real time. By leveraging machine learning algorithms, these systems can detect potential security breaches, unauthorized access, and suspicious activities, enabling swift responses to mitigate risks.
Zero Trust Architecture
Zero Trust Architecture (ZTA) is emerging as a future-forward approach to integration security. ZTA assumes that no entity, whether inside or outside the network, can be trusted inherently. It enforces strict access controls, multi-factor authentication, etc., thereby significantly reducing the attack surface and enhancing overall security.
Container Security
Containerization, mainly using technologies like Docker and Kubernetes, is becoming prevalent for deploying and managing applications. Ensuring container security is crucial, and future trends will focus on enhancing container isolation, vulnerability scanning, and runtime protection.
Conclusion
Integration security works like a shield that fortifies the bridges between systems, ensuring data remains safe and reliable. It helps businesses to embrace integration wholeheartedly while safeguarding valuable data.
And with secure integration solutions like Exalate, businesses no longer need to worry about potential cyber-attacks or data breaches. They can unlock the full potential of interconnected systems, driving growth in the modern business landscape.
Frequently Asked Questions
Why do I need to integrate my applications?
You need to integrate your applications to enable smooth data exchange, streamline business workflows, improve productivity, and provide a unified user experience. Integration allows your systems and teams to work together cohesively, eliminating data silos and enhancing overall efficiency.
What is integration security, and why is it important?
Integration security is securing data during the process of connecting different applications, systems, and platforms. It is essential to safeguard sensitive information, maintain business continuity, comply with regulations, and defend against cyber threats.
How to secure integrations between software applications?
To secure integrations between software applications, you can employ measures such as encryption, secure APIs, authentication, access controls, regular vulnerability scanning, and continuous monitoring. Regularly update software and patches to mitigate potential security risks.
Recommended Reading: