Models are important because they provide us with both a representation of an entity and a template to work with. In the same vein, a Service Integration and Management (SIAM) model provides organizations with guidance on vendor management among multiple suppliers of IT services.
Developing an effective SIAM model entails discovering the best approach for an organization working in a multi-vendor operating model.
This article unpacks what the SIAM operating model involves and how it provides the strategic framework for IT departments to productively manage multiple vendors.
A comprehensive understanding of SIAM is a necessary prerequisite to successfully implementing a SIAM model. So, if you’re still new to SIAM, you can check out our guide on SIAM here first.
Key Takeaways
- SIAM is an operating model that provides a strategic framework for coordinating multiple IT service providers rather than prescribing specific workflows.
- SIAM extends beyond ITSM, while grounded in service management, SIAM covers the entire service lifecycle from idea conception to portfolio management.
- Process alignment across providers is critical because each service provider brings their own practices, so the SIAM model must harmonize these through governance layers and defined interactions.
- SIAM reduces operational risk by spreading responsibilities across multiple providers with clear accountability. Organizations avoid single-vendor lock-in while maintaining control.
- Integration platforms operationalize SIAM tools in order to connect ITSM platforms like ServiceNow, Jira, Freshservice, and Zendesk enable the real-time data flow SIAM governance requires.

What is a SIAM Model?
At its core, SIAM is an IT service delivery model. SIAM can be defined as an “operating model which organizations adopt when working in a multi-service provider model”.
In this model, the SIAM provider is mandated to act on behalf of the business in managing services from multiple IT delivery towers. The purpose of a SIAM model is to ensure IT multisourcing delivery and multisourcing integration are seamless and strategic.
There’s a lot of flexibility in a SIAM operating model, so it’ll also appeal to those seeking a broad set of ideas for implementation.
Below are some of the high-level considerations to kickstart a SIAM process model:
- Processes are an indisputable part of an organization’s SIAM model. Every vendor interaction, escalation path, and service handoff needs a documented process. Without them, multi-vendor environments quickly devolve into finger-pointing when things go wrong.
- Though SIAM relies on processes, SIAM is NOT a process. Think of it as an orchestration layer. SIAM defines how processes from different providers interact, not the processes themselves. This distinction matters because it allows each provider to retain their methodology while still fitting into a coherent whole.
- The SIAM model requires a collaborative approach to be successful. Collaboration here means more than just regular meetings. It requires shared visibility into tickets, synchronized escalation procedures, and integration between service management platforms so data flows without manual handoffs.
- There isn’t a one-size-fits-all approach. Many service providers have their own SIAM model and method of working for each ITIL process. The challenge lies in harmonizing these approaches rather than forcing standardization.
With each service provider bringing their processes, standards, and frameworks, adopting SIAM might seem to be a recipe for disaster. However, SIAM ensures consistency by adopting a best-in-breed, multi-tenant model that will meet business requirements through strategic management.
Achieving an ideal SIAM model for an organization requires governance (strategic, tactical, and operational), management, coordination, and integration. This model can be well adapted for a B2B integration set-up as well. So we must study it in that context.
SIAM vs ITIL vs ITSM: What’s the Difference?
These three terms often appear together, and the confusion is understandable. Here’s how they relate:
ITSM (IT Service Management) focuses on managing IT services for the business. It encompasses the lifecycle activities of IT services: creation, design, delivery, and support. ITSM is about what you do to manage IT services.
ITIL (Information Technology Infrastructure Library) is a framework of best practices for ITSM. It provides guidance on how to implement service management processes effectively. ITIL is about how you should do ITSM.
SIAM (Service Integration and Management) provides governance and control to IT services on behalf of the business, specifically in multi-vendor environments. SIAM is about who manages the overall service delivery when multiple providers are involved.
The relationship works like this: ITSM defines the service management discipline. ITIL provides the best practice framework for implementing ITSM. SIAM coordinates multiple service providers, each of whom may be using ITIL-aligned practices, into a coherent service delivery model.
SIAM wasn’t created to replace ITSM or ITIL. Instead, it addresses the gap that emerged when organizations began sourcing IT services from multiple providers. You can have excellent ITSM practices at each individual provider, but without SIAM, those practices won’t integrate into a seamless service experience for the customer organization.
You can also have a look at how to implement a cross-company integration (across multiple companies) using SIAM and ITIL 4 to get an idea of how they can go hand-in-hand without one replacing the other.
Transitioning to an Operational SIAM Model
To implement SIAM, an organization has to transition to a SIAM model. This will focus on using the high-level considerations highlighted in the previous section, along with an emphasis on multi-service governance.
Most of the attention on building an effective SIAM model will focus on processes. This is because processes are repeated tasks that allow organizations to establish their preferred approach to solving a problem.
But whatever the environment, the SIAM methodology includes the following:
- Practices: The ways of working that guide day-to-day activities. These include service desk operations, incident management procedures, and communication protocols between providers.
- Processes: The structured sequences of activities that deliver specific outcomes. Change management, release management, and problem resolution each follow defined processes.
- Functions: The teams and capabilities that perform specific activities. A security operations center is a function. A network operations center is a function. Each function may span multiple providers.
- Roles: The defined responsibilities within the SIAM ecosystem. Process owners, service managers, and integration coordinators each have specific accountability.
- Structural elements: The organizational components that support SIAM. Governance boards, integration hubs, and shared service centers fall into this category.
Moreover, processes must be allocated to suitable layers in the SIAM model. However, this allocation can differ with each implementation of SIAM. Nevertheless, these processes have to be aligned with other parts of the SIAM model, especially the following:
- SIAM practices
- SIAM layers
- Governance layers
- Structural elements
As part of the overall SIAM model, each party in the SIAM ecosystem has to augment and adapt its process and practices to integrate with the process model.
What a SIAM Operating Model Involves
Too often, SIAM is confined to the process areas described in ITIL, the popular ITSM best practice framework. Though the SIAM process is grounded in service management, SIAM isn’t meant to replace ITSM.
So, how does deploying a SIAM operating model differ from ITSM?
ITSM was created to manage IT services for the business. On the other hand, SIAM was established to provide governance and control to these IT services on behalf of the business. However, SIAM has a broader scope than this.
As we have noted in the service integration and management article, “the topic of supplier management” is more related to SIAM as it covers the entire service lifecycle.
Therefore, SIAM extends beyond the typical incident, problem, and change management to encompass the entire service lifecycle. Its capabilities range from idea conception, and demand management, to service portfolio management, etc.
If we don’t expand the process areas to include ITIL 4 management practices, then these processes can’t be optimized to work in a SIAM operating model.
SIAM implementation requires a collaborative approach because many service providers have their own method of working for each ITIL process.
Organizations should outline their SIAM model with the following in mind to have sustainability:
- Specify principles and policies: Document the rules that govern multi-vendor interactions. This includes data sharing agreements, escalation protocols, and performance standards that apply across all providers.
- Governance framework: Establish the decision-making structure. Who approves changes that affect multiple providers? How are disputes resolved? What metrics determine success?
- Outline roles and responsibilities: Define accountability at every layer. The customer organization, service integrator, and service providers each need clear boundaries to prevent overlap and gaps.
- Process models, practices, and structural elements: Map how work flows through the ecosystem. When a user reports an incident, which provider receives it, how does it escalate, and who owns resolution?
- Outline of services: Catalog what each provider delivers. This clarity prevents assumption gaps where everyone thinks someone else handles a particular service.
- Service providers to be retired: Plan for transitions. SIAM models evolve, and the ability to offboard providers without disrupting service is a sign of model maturity.
The SIAM Model as the Antidote to Large Managed Service Contracts
The explosion of information technology and digitization unleashed an avalanche of IT services upon an organization. IT Service Management (ITSM) emerged to help organizations manage the end-to-end delivery of these IT services.
So, before there was a need for a SIAM model, ITSM already existed. However, ITSM mainly concerns itself with the lifecycle activities of IT services such as its creation, design, delivery, and support.
Moreover, the velocity of change in digital technology would soon usher in another shift in the IT management landscape. With the information technology (IT) ecosystems changing at such a rapid pace, even the most skilled IT generalists were no longer capable of providing its increasingly specialized needs.
As a result of this specialization, outsourcing was needed so organizations could get the expertise they required for sophisticated and niche tasks, especially infrequently used ones. Other factors, such as costs and the need to focus on the core business functions, also accelerated the trend towards outsourcing.
Outsourcing Challenges the SIAM Model Solves
However, the rise of outsourcing didn’t make IT departments obsolete. Most organizations still keep in-house IT professionals who are typically tasked with administrative duties like database management, overseeing the efficacy of networks, and supporting employee IT needs. The rest is typically outsourced to vendors and managed service providers.
But despite their seeming price advantages, single-vendor paradigms soon proved inadequate as one-shop solutions. Furthermore, most single-vendor solutions are insufficient to handle the multitudinous scope of IT problems. In addition, organizations don’t usually want to be held hostage by the rigidity of single vendor lock-in.
Hence, this outsourcing arrangement eventually gave rise to multi-vendor supplier ecosystems, along with an increasingly complex IT value chain. But cracks quickly appeared in this arrangement too.
Organizations soon discovered that their most vexing problems with subcontracting to third parties were:
- Very little transparency: When each provider operates in isolation, the customer organization loses sight of what’s actually happening across the service chain. Tickets disappear into black holes. Status updates arrive late or not at all.
- Not enough quality control on outcomes: Without unified governance, each provider optimizes for their own metrics, which may not align with overall business objectives. Response times look great on paper, while actual user experience suffers.
This new reality, in turn, created the need for supplier management, especially in a multi-source environment.
To be viable, this environment had to provide cross-process, cross-functional, and cross-provider integration where all parties:
- understand their roles, responsibilities, and context in the system,
- are adequately empowered to deliver them,
- and can be held accountable for the outcomes they have been tasked to deliver.
The SIAM model helps an organization outsource IT responsibility so it can focus on its core business. The objective of using SIAM is to enable IT departments to maximize scarce resources through coordinating resources – both internal and external – effectively and efficiently, and in the process, providing the best results and outcomes for an organization.
So, a SIAM model isn’t a theoretical exercise. Rather, it grew from a practical shift towards the outsourcing of specialist resources or skills, which required managing the resultant multiple suppliers of IT services.
Building the Right SIAM Model
As we have seen, SIAM is a service model that exists to provide good practice methods to manage multiple suppliers of IT services.
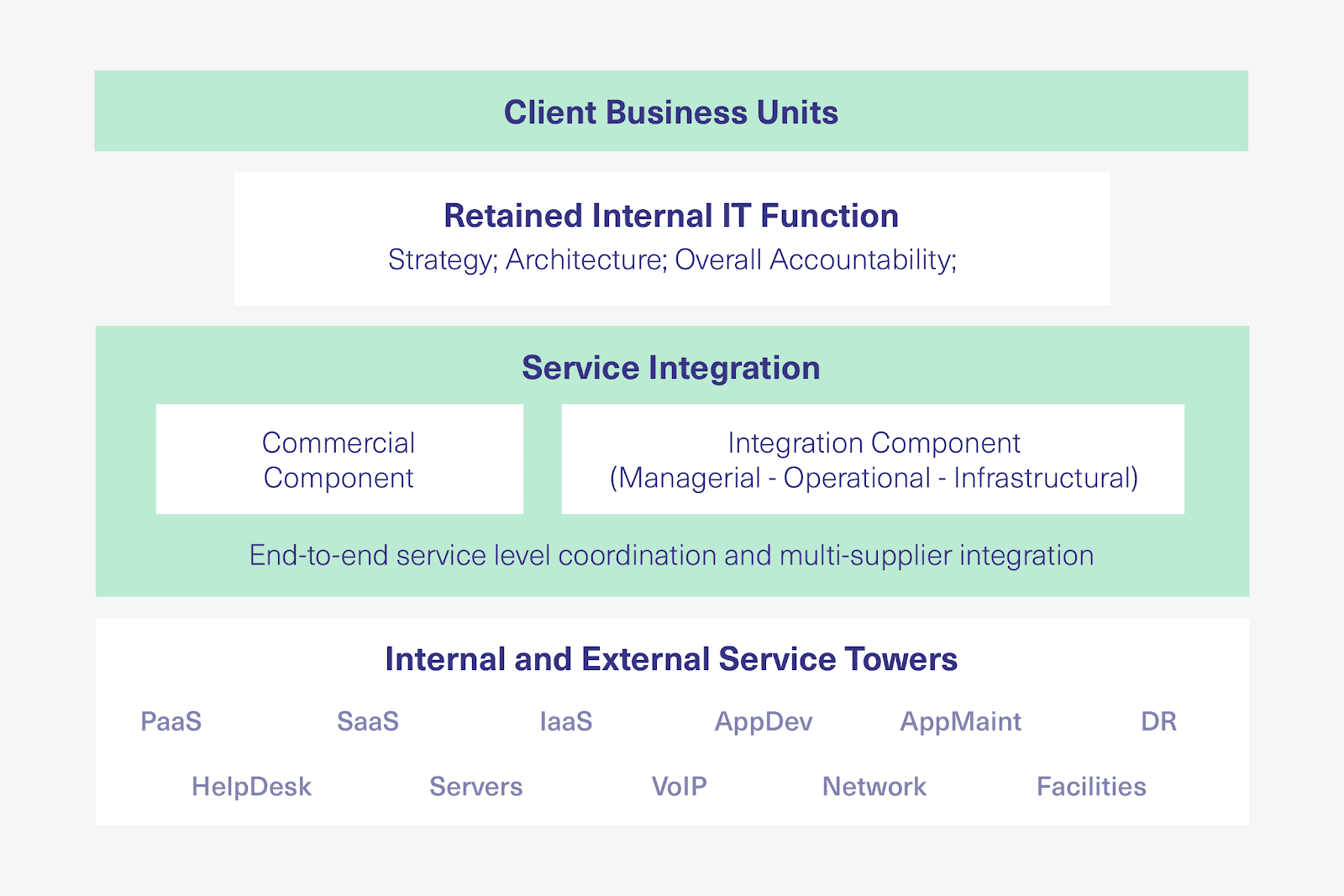
The SIAM ecosystem must include three main layers:
The owner or customer organization (with retained capabilities): This is the singular, accountable role that ensures the process is defined, executed, and evaluated correctly. The customer organization owns the contractual relationships with external service providers and retains certain capabilities internally to maintain strategic control.
- The service integration function: This layer implements an effective cross-service provider organization while providing operational governance to service providers. It’s where end-to-end service governance, integration, management, and coordination are performed.
- Service provider(s): The organizations that actually deliver IT services. Each provider brings their expertise, tools, and processes to the ecosystem.
While the customer organization owns the contractual relationships with external service providers, the service integration function is where end-to-end service governance, integration, management, and coordination are performed.
Service Integrator
The service integrator role can be carried out by one or more organizations, including the customer organization. Regardless of the number of organizations providing this role, it should still be considered as a single logical service integrator.
Based on the configuration of the service integrator, four SIAM models align with the most common situations adopted by organizations:
- Internal service integrator
- External service integrator
- Hybrid service integrator
- Lead suppliers as service integrators
The service integrator is the most important role in the SIAM model. This is because SIAM’s process execution is likely to involve multiple stakeholders who don’t have homogenous practices, tools, processes, and documents.
Although service providers have their respective processes, they nonetheless have to be integrated as part of an overall model with defined rules, interactions, and controls.
This is complex and requires a service integrator to manage integration across diverse providers. The service integrator has to navigate a moving technological landscape, processes across provider networks, several service management frameworks and practices, diverse corporate cultures with every ecosystem member, and juggle complex contractual and personal relationships.
Internal Service Integrator
In this model, internal control is the name of the game. Here, the control of vendors is in-house and not outsourced to any third party.
The advantage of this model is its cost-effectiveness. However, for it to work effectively, a single logical entity has to be charged with its implementation. They also need to have sufficient authority to carry out their role; otherwise, this model is unlikely to produce the expected results.
Because it’s inside the organization, it’s often managed through targets and internal agreements.
Best for: Organizations with strong internal IT capabilities that want maximum control over vendor relationships and have the resources to staff an integration function.
External Service Integrator
In this SIAM model, an independent service integrator – likely a specialist – is responsible for managing vendor relationships on behalf of the customer organization.
This service provider isn’t part of the customer organization. As such, its performance is usually managed through a contract with the customer organization and service level agreements.
Best for: Organizations that lack internal expertise in multi-vendor management or prefer to outsource this complexity to specialists.
Hybrid Service Integrator
This approach combines both the internal and external service provider models. In this mode, the responsibilities of the service integrator are spread across the customer organization and one of the service providers.
In practice, the configuration might look like this: the client mandates an internal resource group to manage the smaller vendors while an external service integrator handles the relationship with the more critical vendors.
Best for: Large organizations with tiered vendor relationships where some providers are strategic partners requiring specialist oversight, while others are commodity suppliers that internal teams can manage.
Lead Supplier as Service Integrator
In this model, one of the existing service providers becomes responsible for the management of other vendors, in addition to their existing service delivery role. To pull off this kind of arrangement, there needs to be a high degree of trust between the customer organization and the service provider.
Best for: Organizations with a dominant strategic partner who has demonstrated the capability and trustworthiness to manage peer providers fairly.

The Technology Foundation for SIAM: Integration Platforms
A SIAM model depends on information flowing seamlessly between the customer organization, the service integrator, and all service providers. Without technology that enables this flow, SIAM governance becomes administrative overhead rather than operational reality.
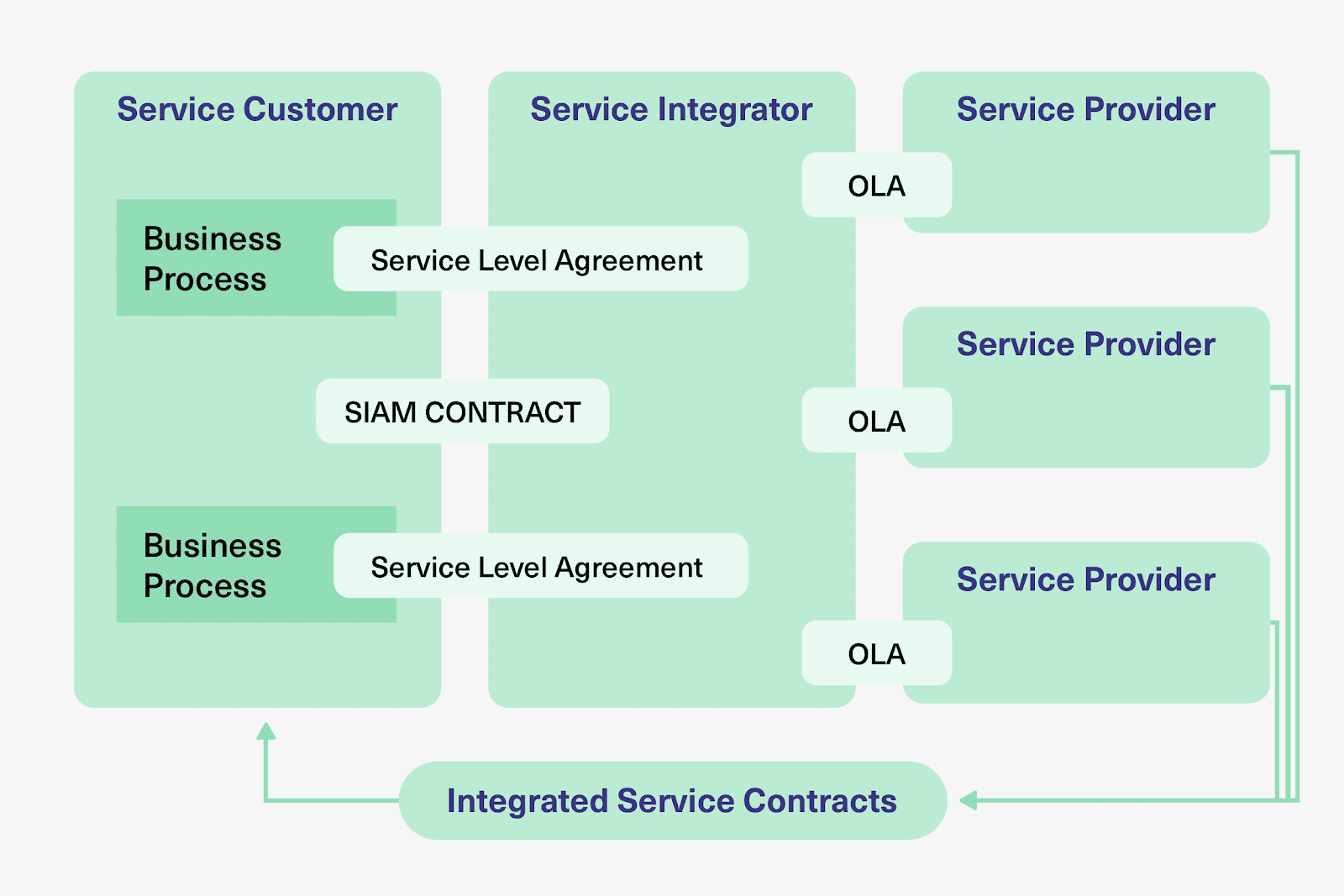
Integration platforms connect the ITSM tools used by different providers—ServiceNow, Jira Service Management, Freshservice, Freshdesk, Zendesk, and Azure DevOps among them. These platforms synchronize tickets, statuses, and updates in real-time so that all parties work from consistent information.
Consider an incident that requires coordination between a cloud infrastructure provider using ServiceNow and an application support team using Jira.
Without integration, someone must manually copy ticket details between systems, introducing delays and errors. With integration, the ticket exists in both systems simultaneously, updates propagate automatically, and resolution time drops.
The integration platform becomes the nervous system of the SIAM model, carrying signals between providers and enabling the coordinated response that SIAM governance demands.
When evaluating integration options for SIAM environments, consider these capabilities:
- Bidirectional synchronization so changes in any system propagate to connected systems
- Flexible field mapping to handle different data structures across providers
- Security certifications (ISO 27001:2022, SOC 2 Type II) appropriate for enterprise environments—check the vendor’s Trust Center for compliance documentation
- Support for cross-company connections that respect organizational boundaries while enabling collaboration
- Custom connector capabilities for proprietary systems via REST APIs
Platforms like Exalate address these requirements, connecting platforms across different organizations while giving each side independent control over what data they share.
AI-assisted configuration through tools like Aida (Exalate’s documentation assistant) simplifies the setup of complex multi-provider integrations.

Calculate time and money savings from automated bidirectional sync.
SIAM Model Implementation: Practical Use Cases
Case 1: Multi-Cloud Provider Coordination
Challenge: A financial services firm uses AWS for core banking applications, Azure for analytics workloads, and GCP for machine learning projects. Each cloud provider has a managed services agreement with different support teams. When a performance issue affects multiple clouds, the firm can’t get a coordinated response.
Solution: The firm implements a SIAM model with an internal service integrator who has visibility across all three cloud relationships. They deploy integration that connects the ticketing systems of all providers, enabling automatic escalation when issues span multiple environments.
Real-world application: A latency spike in the analytics pipeline triggers alerts in both AWS (source data) and Azure (processing). The integration automatically creates correlated tickets in both providers’ systems while the internal service integrator coordinates the investigation. Root cause identification drops from days to hours because both teams see the same timeline.
Case 2: MSP Client with Multiple Specialized Vendors
Challenge: A manufacturing company outsources IT to an MSP for general operations, but uses specialized vendors for ERP (SAP), cybersecurity (managed SOC), and IoT platform management. The MSP can’t see security incidents, and the SOC can’t correlate security events with operational changes.
Solution: The company positions its MSP as a lead supplier service integrator, with integration connections to the specialized vendors. Freshservice (MSP) connects to the SOC’s ServiceNow instance and the ERP team’s Jira Service Management.
Real-world application: A security alert from the SOC correlates with a recent ERP change. Because the MSP sees both the security ticket and the change record through integration, they can immediately assess whether the change caused the vulnerability and coordinate rollback across teams without waiting for separate conference bridges.
Case 3: Government Agency with Strict Compliance Requirements
Challenge: A government agency must maintain separation between departments while enabling shared IT services. Their SIAM model needs to respect data classification requirements while still enabling cross-departmental coordination on infrastructure issues.
Solution: The agency implements a hybrid service integrator model where the central IT organization manages common infrastructure providers, but each department retains control over its application-specific vendors. Integration between Zendesk (central IT) and department-specific Freshdesk instances uses selective field mapping that strips classified information.
Real-world application: A network outage affects multiple departments. Central IT creates a master incident, and the integration creates corresponding tickets in each affected department’s system, but only with network topology information, not content about what each department was doing when the outage occurred. Departments see status updates without gaining visibility into each other’s operations.
The Complexity and Challenge of the SIAM Process Model
A SIAM model must clearly define the policies and principles, establishing ownership of the roles and responsibilities for these three layers.
Although the SIAM model is a process, SIAM transcends end-to-end process management. So, the role of process management isn’t diminished within SIAM. On the contrary, SIAM adds more depth to process management since process execution is likely to involve multiple stakeholders.
Because of such complexity, it’s necessary to give heightened focus to clearly defining roles and responsibilities following these key principles:
- All definitions should be relevant to the SIAM model. Generic job descriptions won’t work. Each role definition must specify how that role interacts with other providers and the service integrator.
- Each defined role must include the necessary knowledge, skills, competencies, and capabilities. SIAM environments require people who can work across organizational boundaries, not just within their own provider’s hierarchy.
- Integration and collaboration capabilities must be included in the definitions where appropriate. Technical staff need to understand how their systems connect to others. Managers need to coordinate across provider boundaries.
- The customer organization, the service integrator, and the service providers must each have separate definitions of roles to ensure there’s no duplication or overlap. When responsibilities are ambiguous, accountability suffers.
The Key Benefits of a SIAM Model
SIAM can be used globally and in various organizations since it applies to more than just IT services. This is relevant to any environment where services are sourced from a number of service providers.
However, the added benefit of SIAM is that we can derive inspiration from “other best practices, frameworks, methodologies, and standards used for IT and ITSM.”
These advantages that accrue to the SIAM model should encourage organizations to adopt it:
- Reduces operational risk: Instead of relying on a single service provider, the SIAM model provides organizations with the guardrails to spread operational risks across multiple service providers. When one provider fails, others continue operating, and the service integrator coordinates recovery.
- Greater access to expertise: The SIAM model enables organizations to gain access to “best-in-class” skills across a wider range of technologies from a broader range of suppliers. You can engage the leading provider for each technology domain rather than accepting a single vendor’s competency across all areas.
- Agility in meeting demands: Provides organizations with the ability to respond and meet the increasingly complex demands of business. New requirements can be addressed by engaging new specialists without disrupting existing provider relationships.
- Increased accountability: SIAM contracts and their scope provide greater transparency and allow organizations to hold service providers accountable for their part of the end-to-end service chain. Clear boundaries make it obvious where failures occur.
- Increased flexibility and nimbleness: SIAM provides organizations with the ability to adapt to a flexible model that allows service providers to be onboarded and offboarded easily. Technology changes, and your provider portfolio should change with it.

FAQs
What is a SIAM model in simple terms?
A SIAM model is an operating framework that helps organizations manage multiple IT service providers as a coordinated ecosystem rather than isolated vendor relationships. It establishes governance, processes, and accountability structures so that services from different providers integrate smoothly and deliver consistent outcomes for the business.
What are the four types of SIAM models?
The four main types are: internal service integrator (customer organization manages vendors in-house), external service integrator (independent specialist manages vendor relationships), hybrid service integrator (responsibilities split between internal teams and external specialists), and lead supplier as service integrator (a trusted vendor manages peer providers alongside their own service delivery).
How is SIAM different from ITIL?
ITIL is a framework of best practices for IT service management—it tells you how to run service management processes effectively. SIAM is an operating model for coordinating multiple service providers who may each use ITIL-aligned practices. ITIL focuses on what good service management looks like; SIAM focuses on who coordinates service delivery when multiple providers are involved.
What role does integration technology play in SIAM?
Integration platforms are the operational foundation that makes SIAM governance practical. They connect the different ITSM tools used by providers (ServiceNow, Jira, Freshservice, Zendesk, and others), synchronize tickets and updates in real-time, and give the service integrator visibility across the entire provider ecosystem. Without integration, SIAM becomes administrative overhead rather than operational coordination.
What is the service integrator role in SIAM?
The service integrator coordinates activities across all service providers, ensuring they work together as a coherent service delivery ecosystem. This role manages cross-provider processes, resolves conflicts, maintains unified visibility, and enforces the governance framework. The service integrator can be internal, external, or a combination—but it must function as a single logical entity.
How do organizations choose which SIAM model to implement?
The choice depends on internal capabilities, provider portfolio complexity, and control preferences. Organizations with strong IT teams often choose internal service integrators. Those lacking multi-vendor management expertise may prefer external specialists. Large enterprises with tiered vendor relationships frequently adopt hybrid models. The lead supplier model works when a trusted strategic partner can fairly manage peer providers.
What are the main challenges in SIAM implementation?
The biggest challenges are process harmonization across providers with different practices, establishing clear accountability without overlap, maintaining visibility across organizational boundaries, and ensuring the technology infrastructure supports real-time information sharing. Cultural resistance from providers who prefer operating independently also slows implementation.
Can SIAM work for small and medium businesses?
Yes, though the model scales appropriately. Small businesses with just two or three providers may not need formal service integrator roles but still benefit from SIAM principles: defined responsibilities, clear escalation paths, and integration between provider systems. The governance overhead of full SIAM implementation makes more sense as vendor complexity increases.
Recommended Reads:
- Service Integration and Management (SIAM)
- The Definitive Guide to Cross-Company Integrations for IT Professionals
- B2B Integration (business-to-business integration)
- eBonding Integration: The Ultimate Guide to Flexible Data Sync
- Service Integration and Management: an Introduction to SIAM (podcast)
- ITIL and Cross-Company Integration (podcast)