
Your Data, Our Priority
Unmatched Security for Peace of Mind
Exalate is built with security at its core. Every aspect, from product design to data management, is carefully crafted for your protection.
Secure by design
Exalate employs a multi-layered strategy to safeguard customer data and ensure its confidentiality. We implement security vulnerability scanning at every phase of development, deployment, and operation to maintain robust protection.
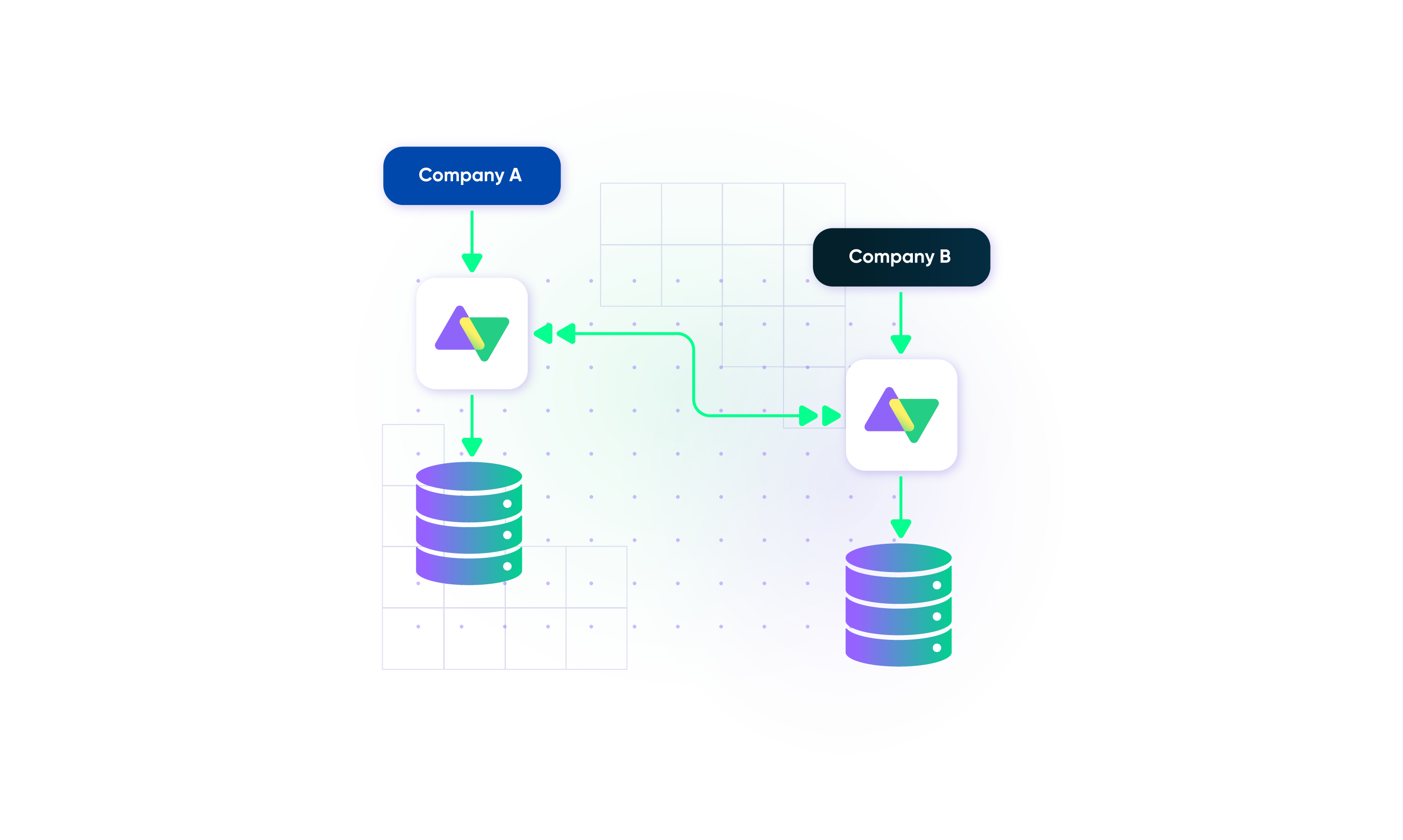
Decentralized Integration
In a decentralized integration setup, each side has full and independent control over the data it sends and receives. This approach enhances security and privacy by ensuring shared data remains safe from unauthorized access. It also removes single points of failure and makes the integrated systems more scalable and loosely connected, reducing unwanted dependencies.
Single-tenant Architecture
In integration software, a single-tenant application is linked to just one system, whereas a multi-tenant application connects several systems through a shared infrastructure. Due to the complexity and potential risks of integration, single-tenant architecture helps prevent information leakage by keeping data isolated at the infrastructure level. This approach improves security and lowers the risk of data breaches.
Data Encryption
Any payload data in the Exalate cloud is encrypted in transit and at rest.
Data Privacy
Exalate is GDPR-compliant and designed with privacy in mind. All integrating parties have independent and full control over the transmitted data ensuring privacy at every step.
Authentication
Exalate uses OAuth2 or token-based authentication mechanisms where applicable.
Proudly ISO 27001:2022 Certified
Our ISO 27001:2022 certification guarantees top-notch security measures to protect your data from threats and unauthorized access. We adhere to international standards and fully comply with legal requirements. Through continuous improvement, we keep our security practices ahead of emerging trends.

A Deep Dive into Exalate Security and Architecture
Discover how Exalate ensures secure and controlled synchronization across multiple trackers. Understand how information is processed by different components and how it flows through the system. Learn about our security measures, information flow, and key components.

Security FAQs
Answer to common questions.
For more, check:
Exalate is NOT a data processor as defined in GDPR Art 4. Exalate can be compared to an email system, which processes synchronization transactions as fast as possible. Exalate has not been designed for processing PII data (ie., there are no tables with user-related information). Exalate can fully operate, even if there is no PII data in the messages.
A single-tenant application, in the context of integration software, is an application that is related to only one system. A multi-tenant application on the other hand allows using one infrastructure to connect with multiple systems. So, whenever considering an integration solution, one should pay attention to the tenancy of the proposition.
All software has bugs, either because of improper development, configuration mistakes, or any other reason. The recent breaches at LastPass and Octa show that protecting information is a Herculean task. Integration software is more complex as it needs to take care of many diverse aspects and information paths.
To minimize the risk of information leakage, a single-tenant architecture is a much better option as it allows us to contain information leaks at the infrastructure level.
When an Exalate node is deployed on the Exalate Cloud, it is running inside a ‘Kubernetes pod’ that is configured to ensure no information can leak. The maintenance of this Exalate Cloud is fully based on the principles of ‘Infrastructure as Code’. There is no manual configuration for the environment.
All clusters are protected by state-of-the-art Endpoint Detection and Response (EDR) systems, specifically the ‘Cortex MDR’, from Palo Alto. This infrastructure is monitored round-the-clock by a Security Operations Center (SOC) staffed by Cyber Security engineers. The monitoring service, provided by NVISO, has been validated by a MITRE ATT&CK test.
Exalate uses the Transport Layer Security (TLS) Protocol Version 1.3. If the issue tracker does not support this version, we use TLS 1.2.
Once the Connection setup is finished, Exalate generates the shared secret. The secret is used to define a secure connection between both Instances. It is shared only once to generate a JWT token. The token is temporary and is generated for every communication request between Exalate in both Instances.
The following information is exchanged between Instances:
- shared secret
- information about the type of connection with the Destination instance
- Connection name
- information about the Connection initiator
- Exalate app version, including supported features
- Instance type and version ( JIRA Server, JIRA Cloud or HP ALM/QC)
- Instance URL and Exalate URL
- Instance UID, which is a unique instance identifier
Vulnerabilities are handled according to the ISO27001:2022 standard. Customers are notified of critical vulnerabilities.
No. Exalate does not store any PII data directly.